Occasionally, I get a notification, from my favorite social networking site or my mortgage company, starting out with the words, “We respect your privacy.” Translation: “We respect the economic value of your personal information.” The notification typically continues with how my personal information is shared with affiliates, who may, at their discretion, share my personal information with other affiliates. They go on to explain that I am free to “opt-out” of [some of] these disclosures, and, should I chose to do so (after my information is already “out”) , “opt-out” separately with each affiliate, subject to their own privacy policies. Of course, these privacy policies are subject to change without notice.
If this situation does not strike you as sheer lunacy, an illustration is in order.
Imagine this. Frank and Jesse James walked into a bank with their affiliates Willie Sutton and Bonnie & Clyde. They fired several shots into the air and started to round up hostages and demand money. Immediately, the bank guard approached Frank and Jesse with a clipboard with a Bank Robbery Opt-out Form attached. Frank looked at the completed form, and said, “Everything appears to be in order. Since my brother and I are honorable people, we will honor your opt-out request. You will, however, need to opt-out separately with our affiliates.”
Next, the guard approached Bonnie with a Bank Robbery Opt-out Form. Bonnie took one look at the form and responded, “Clyde and I would be delighted to honor your opt-out request. Oh, my! Look at the time: It’s after four on Friday afternoon. Our opt-out system is down for the weekend. Come back on Monday, and we will honor your request. In the meantime, we have a bank robbery to attend to.”
Before the guard had a chance to approach Willy Sutton with the third Bank Robbery Opt-out Form , Frank mentioned that he and Jesse had just changed their Bank Robbery Opt-out Policy, and would be rejoining their affiliates’ bank robbery in progress.
Hopefully, now you understand that privacy opt-out policies are often designed to prevent you from opting-out. They monetize your personal information and trample on your privacy rights. I suggest you demand stronger privacy protection laws and regulations from our state and federal elected officials and regulators. More information is available through the Privacy Rights Clearinghouse, with whom I am not affiliated.
 99.999% sure that no bank would ever send an email with a .html attachment. After updating Norton and Malwarebytes, I got clean scans of the attachment from both. Even though all the links in the email were to Wells Fargo, I was certain that the attachment had malicious intent, and uploaded it to Virus Total, and 1 of the 57 online scanners, 56 gave a green check mark, and 1 correctly said Heuristics.Phishing.Email.SpoofedDomain.
99.999% sure that no bank would ever send an email with a .html attachment. After updating Norton and Malwarebytes, I got clean scans of the attachment from both. Even though all the links in the email were to Wells Fargo, I was certain that the attachment had malicious intent, and uploaded it to Virus Total, and 1 of the 57 online scanners, 56 gave a green check mark, and 1 correctly said Heuristics.Phishing.Email.SpoofedDomain.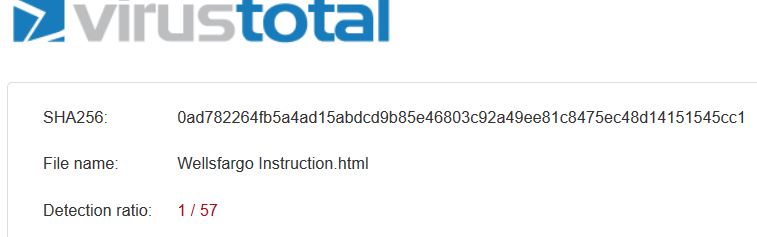 Had the attachment been a virus or trojan, the detection rate may have been much higher. Regardless, be careful. Don’t think that your security software will protect you from willy-nilly clicking on attachments, because it may not. I have had other instances of attached trojans getting clean scans. Only after I uploaded them to my security software vendor did they analyze and update their software to detect and remove them. It’s dangerous out there.
Had the attachment been a virus or trojan, the detection rate may have been much higher. Regardless, be careful. Don’t think that your security software will protect you from willy-nilly clicking on attachments, because it may not. I have had other instances of attached trojans getting clean scans. Only after I uploaded them to my security software vendor did they analyze and update their software to detect and remove them. It’s dangerous out there.